- Регистрация
- 17 Февраль 2018
- Сообщения
- 38 866
- Лучшие ответы
- 0
- Reactions
- 0
- Баллы
- 2 093
Offline
Official was connected to FBI probe of cartel kingpin Joaquín “El Chapo” Guzmán.


Bloomberg's Best Photos 2014: Drug trafficker Joaquin "El Chapo" Guzman is escorted to a helicopter by Mexican security forces at Mexico's International Airport in Mexico city, Mexico, on Feb. 22, 2014. Photographer: Susana Gonzalez/Bloomberg via Getty Images Credit: Getty Images
The Sinaloa drug cartel in Mexico hacked the phone of an FBI official investigating kingpin Joaquín “El Chapo” Guzmán as part of a surveillance campaign “to intimidate and/or kill potential sources or cooperating witnesses,” according to a recently published report by the Justice Department.
The report, which cited an “individual connected to the cartel,” said a hacker hired by its top brass “offered a menu of services related to exploiting mobile phones and other electronic devices.” The hired hacker observed “'people of interest' for the cartel, including the FBI Assistant Legal Attache, and then was able to use the [attache's] mobile phone number to obtain calls made and received, as well as geolocation data, associated with the [attache's] phone."
“According to the FBI, the hacker also used Mexico City's camera system to follow the [attache] through the city and identify people the [attache] met with,” the heavily redacted report stated. “According to the case agent, the cartel used that information to intimidate and, in some instances, kill potential sources or cooperating witnesses.”
The report didn't explain what technical means the hacker used.
Existential threat
The report said the 2018 incident was one of many examples of “ubiquitous technical surveillance” threats the FBI has faced in recent decades. UTS, as the term is abbreviated, is defined as the “widespread collection of data and application of analytic methodologies for the purpose of connecting people to things, events, or locations.” The report identified five UTS vectors, including visual and physical, electronic signals, financial, travel, and online.
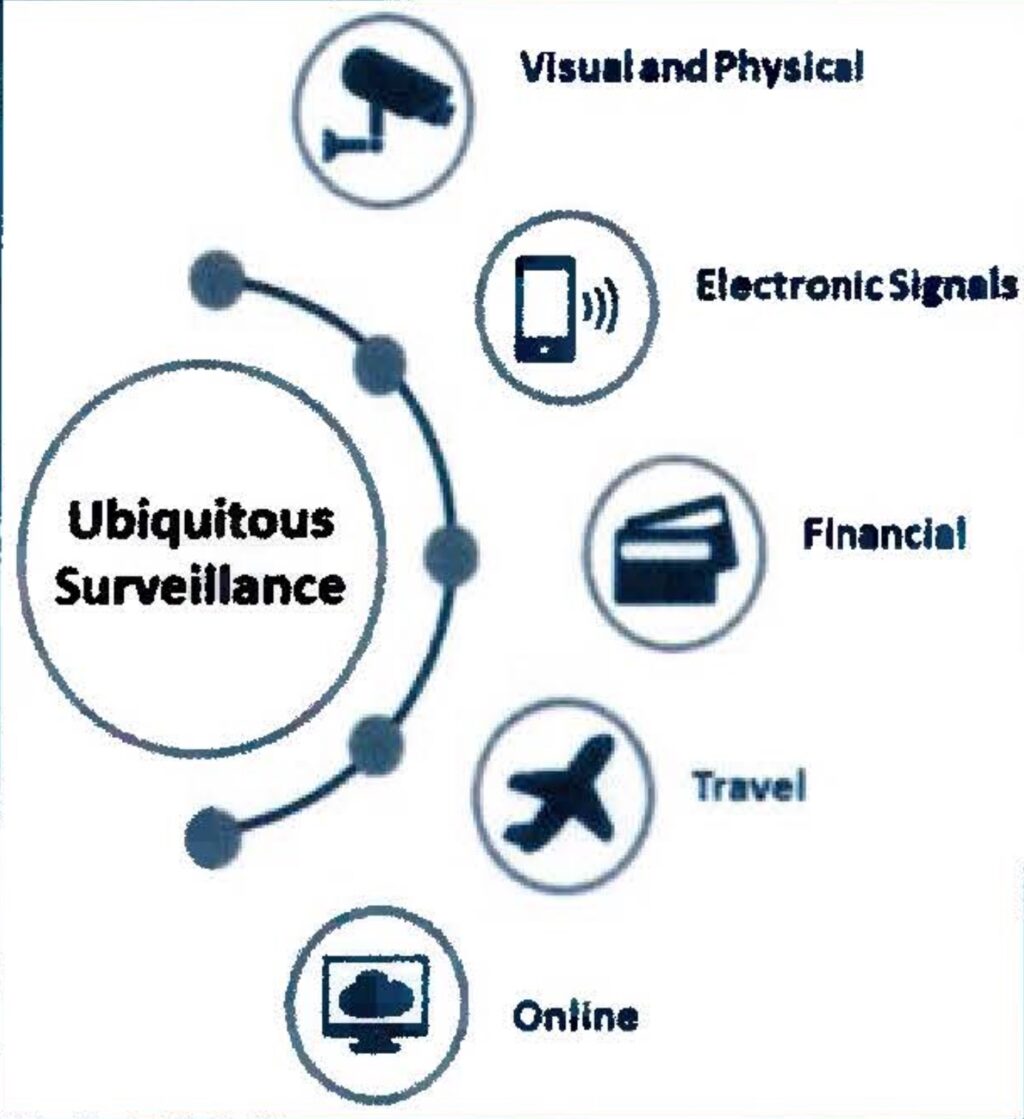
Credit: Justice Department
While the UTS threat has been longstanding, the report authors said, recent advances in commercially available hacking and surveillance tools are making such surveillance easier for less sophisticated nations and criminal enterprises. Sources within the FBI and CIA have called the threat “existential,” the report authors said
A second example of UTS threatening FBI investigations occurred when the leader of an organized crime family suspected an employee of being an informant. In an attempt to confirm the suspicion, the leader searched call logs of the suspected employee’s cell phone for phone numbers that might be connected to law enforcement.
A third example of the UTS threat is the use of credit or debit card transaction reports compiled by commercial data brokers.
“Though this data is anonymized, in 2015, researchers from the Massachusetts Institute of Technology found that with the data from just four transactions, they could positively identify the cardholder 90% of the time,” report authors wrote.
Remaining examples of UTS threats were redacted.
In a 2022 memorandum, the FBI exposed what it said was a “disjointed and inconsistent” response to the threat. It went on to call for improving training across the FBI. The latest report said procedures put in place following the 2022 memorandum were inadequate. It also went on to note the FBI encountered a data breach in recent years that also aided UTS efforts. The report said there were “gaps in the FBI's policies and procedures for how to respond to such a breach.” Details about the breach and the response were redacted from the public document.
The report recommended the following actions be taken:
1. (U) Thoroughly document and incorporate all identified UTS vulnerabilities into its final UTS mitigation plan, including those identified in the Anatomy of a Case.
2. (U) Finalize its UTS Strategic Plan to include strategies for coordinating disparate UTS efforts found across the enterprise and leveraging existing resources that are already in place to address the evolving risks posed by UTS. In addition, the new Strategic Plan should ensure that FBI officials who have the authority to execute the strategy are identified and are empowered to ensure that the FBI has clear and unambiguous UTS-related policies throughout the enterprise.
3. (U) Establish a clear line of authority for responding to enterprise-wide, UTS-related incidents to ensure a coordinated response.
4. (U) Assess its ability to further expand the availability of its advanced UTS-related training modules and take any necessary additional steps to ensure all personnel are and remain adequately trained on both the basic and advanced skills they need to address the evolving UTS threat.
Mexican drug cartels have long employed sophisticated technical means to track law enforcement officials and conceal their own internal activities.


Bloomberg's Best Photos 2014: Drug trafficker Joaquin "El Chapo" Guzman is escorted to a helicopter by Mexican security forces at Mexico's International Airport in Mexico city, Mexico, on Feb. 22, 2014. Photographer: Susana Gonzalez/Bloomberg via Getty Images Credit: Getty Images
The Sinaloa drug cartel in Mexico hacked the phone of an FBI official investigating kingpin Joaquín “El Chapo” Guzmán as part of a surveillance campaign “to intimidate and/or kill potential sources or cooperating witnesses,” according to a recently published report by the Justice Department.
The report, which cited an “individual connected to the cartel,” said a hacker hired by its top brass “offered a menu of services related to exploiting mobile phones and other electronic devices.” The hired hacker observed “'people of interest' for the cartel, including the FBI Assistant Legal Attache, and then was able to use the [attache's] mobile phone number to obtain calls made and received, as well as geolocation data, associated with the [attache's] phone."
“According to the FBI, the hacker also used Mexico City's camera system to follow the [attache] through the city and identify people the [attache] met with,” the heavily redacted report stated. “According to the case agent, the cartel used that information to intimidate and, in some instances, kill potential sources or cooperating witnesses.”
The report didn't explain what technical means the hacker used.
Existential threat
The report said the 2018 incident was one of many examples of “ubiquitous technical surveillance” threats the FBI has faced in recent decades. UTS, as the term is abbreviated, is defined as the “widespread collection of data and application of analytic methodologies for the purpose of connecting people to things, events, or locations.” The report identified five UTS vectors, including visual and physical, electronic signals, financial, travel, and online.

Credit: Justice Department
While the UTS threat has been longstanding, the report authors said, recent advances in commercially available hacking and surveillance tools are making such surveillance easier for less sophisticated nations and criminal enterprises. Sources within the FBI and CIA have called the threat “existential,” the report authors said
A second example of UTS threatening FBI investigations occurred when the leader of an organized crime family suspected an employee of being an informant. In an attempt to confirm the suspicion, the leader searched call logs of the suspected employee’s cell phone for phone numbers that might be connected to law enforcement.
A third example of the UTS threat is the use of credit or debit card transaction reports compiled by commercial data brokers.
“Though this data is anonymized, in 2015, researchers from the Massachusetts Institute of Technology found that with the data from just four transactions, they could positively identify the cardholder 90% of the time,” report authors wrote.
Remaining examples of UTS threats were redacted.
In a 2022 memorandum, the FBI exposed what it said was a “disjointed and inconsistent” response to the threat. It went on to call for improving training across the FBI. The latest report said procedures put in place following the 2022 memorandum were inadequate. It also went on to note the FBI encountered a data breach in recent years that also aided UTS efforts. The report said there were “gaps in the FBI's policies and procedures for how to respond to such a breach.” Details about the breach and the response were redacted from the public document.
The report recommended the following actions be taken:
1. (U) Thoroughly document and incorporate all identified UTS vulnerabilities into its final UTS mitigation plan, including those identified in the Anatomy of a Case.
2. (U) Finalize its UTS Strategic Plan to include strategies for coordinating disparate UTS efforts found across the enterprise and leveraging existing resources that are already in place to address the evolving risks posed by UTS. In addition, the new Strategic Plan should ensure that FBI officials who have the authority to execute the strategy are identified and are empowered to ensure that the FBI has clear and unambiguous UTS-related policies throughout the enterprise.
3. (U) Establish a clear line of authority for responding to enterprise-wide, UTS-related incidents to ensure a coordinated response.
4. (U) Assess its ability to further expand the availability of its advanced UTS-related training modules and take any necessary additional steps to ensure all personnel are and remain adequately trained on both the basic and advanced skills they need to address the evolving UTS threat.
Mexican drug cartels have long employed sophisticated technical means to track law enforcement officials and conceal their own internal activities.
