In the days of tech yore, antivirus software was just that. You installed the application and let it scan your system for malware.
But as protecting your PC became more complicated, vendors slowly morphed their offerings into full suites. Nowadays, a firewall and other safeguards like a browser extension, password manager, and VPN get dropped onto your system. You might even get a handful of utilities focused on optimizing your computer, rather than defending it.
To help you figure out what components are most important — as well as necessary for your situation — we’ve broken down the most common elements of today’s antivirus software.
Antivirus
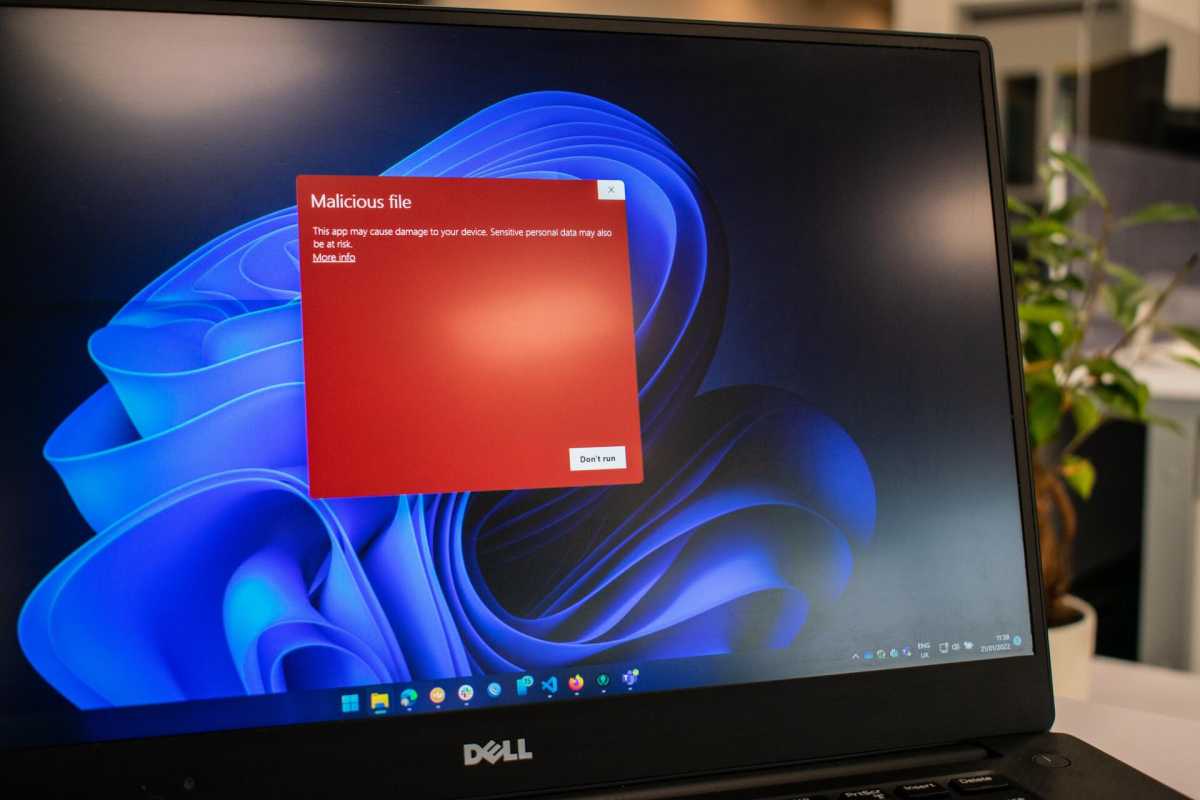
At the heart of every antivirus plan is the engine that detects threats to your PC. These days, modern antivirus software both anticipates and roots out the presence of viruses and other malware, including ransomware.
Blocking malware before it even hits your computer is a key defense against situations like your PC being commandeered for botnet attacks, having your data stolen, and getting locked out of your documents and folders. It also can stop creepy behavior like being spied on through your webcam or having everything you do recorded (including what you type).
An antivirus engine does this by screening the websites you visit, as well as the email and apps on your PC, for phishing links and potential malicious downloads. Phishing attempts usually try to steal your passwords, credit card details, or other personal information by pretending to be a legitimate site and then capturing whatever data you input.
Ed Hardie
Ed Hardie
Ed Hardie
The other half of the protection comes from the antivirus engine’s ability to detect and then eliminate malware that does land on your PC. Typically, this monitoring happens in at least two forms: Real-time scanning watches for changed or new files, as well as unusual behavior from apps and Windows itself. Scheduled scans (especially if they’re full system scans) dig into your PC to make sure nothing was missed by the real-time scanning.
Antivirus apps and virus definitions get continual updates as new malware appears in the wild. So long as you buy a subscription from a reputable company (like those reviewed by leading security organizations AV-Test and AV-Comparatives), you’ll be kept up to date for your whole term. That applies even if you bought a plan labeled as 2024 and the year crosses over into 2025.
The plan you buy will dictate how many devices are covered — usually subscriptions support macOS, Android, and iOS gear in addition to Windows PCs. On rare occasion, Chromebooks are supported as well.
Firewall
Traffic doesn’t just go to your computer, but from it, too — and depending on the app, that data may contain info you don’t want to fall into the wrong hands. A malicious app can spy on what you’re doing, and then transmit that to a would-be hacker. A good firewall blocks those attempts automatically.
A reliable firewall also closes networking ports on your PC, so that unknown parties can’t connect and find a way into your home network. Think of it like a house where shutting the external doors causes them to blend into the walls, making it difficult to discern. However, if a door is left open, someone could walk in and then take what they want, set up cameras to spy on you, or change your phone settings to forward all text messages to them, among other things. A firewall is a bit like a guard that always stays alert, making sure no one can get in.
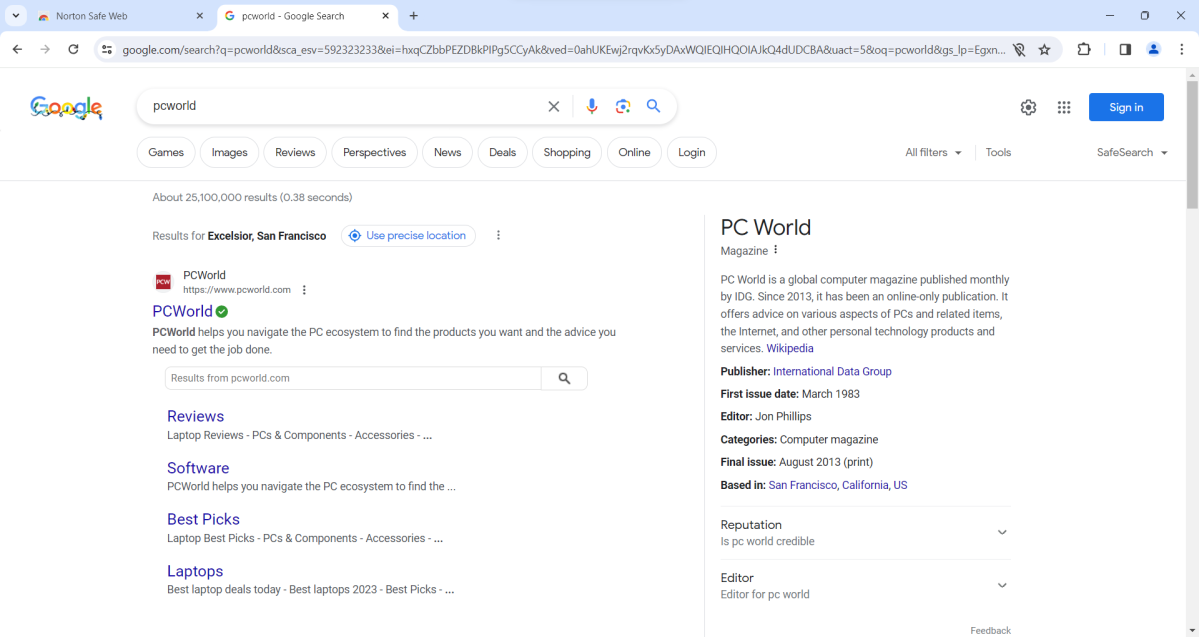
Browser extensions
The most common add-on to your browser (be it Edge, Chrome, or Firefox) is one designed for online protection. Usually, it’ll at least add extra icons to search results to warn you away from suspicious sites. The better ones also block trackers and ads to defend your privacy and help you avoid malvertising — that is, malware spread through compromised ad networks.
PCWorld
PCWorld
PCWorld
Other extensions help tie your browser into components of the overall antivirus suite, making their use seamless. Most often you’ll see one for a password manager get installed, so that you can capture, create, and use entries in your vault.
On occasion, you’ll see antivirus suites that offer plugins for shopping coupons and deals. These are not related to security at all, and can actually conflict with keeping your privacy.
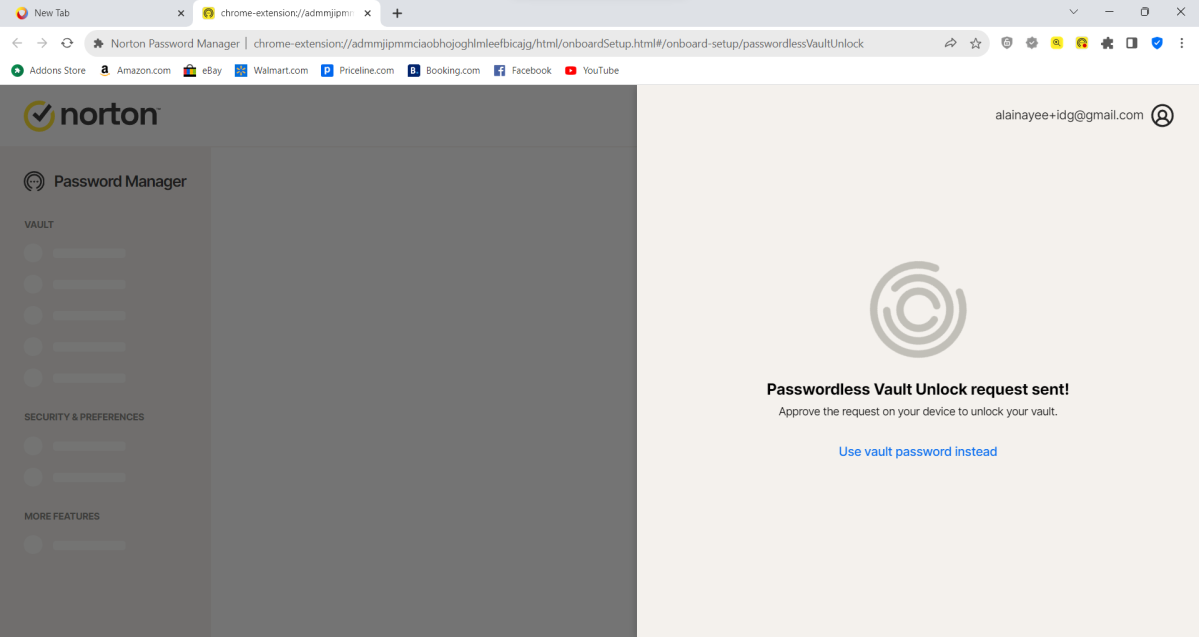
Password manager
These days online security extends beyond simply defending your PC against malware. That’s why today’s software also blocks phishing websites, which generally try to capture sensitive information (like your login info) by pretending to be a legitimate site. If your credentials get stolen, you could end up with problems ranging from unwanted credit card purchases all the way to full-blown identity theft.
By using a password manager, you can prevent the simplest form of account hacking — credential stuffing. A bad actor takes usernames and passwords leaked through data breaches, then tries them across the web to see what else can be accessed with that same login info. Since some people reuse their passwords, attackers can breach a whole new set of accounts easily.
PCWorld
PCWorld
PCWorld
Password managers let you generate strong, unique credentials, which thwarts this kind of hack. They also take away the burden of trying to remember dozens (if not hundreds) of secure passwords. And with data leaks and breaches so commonplace nowadays, these services make changing your password far simpler and faster, too.
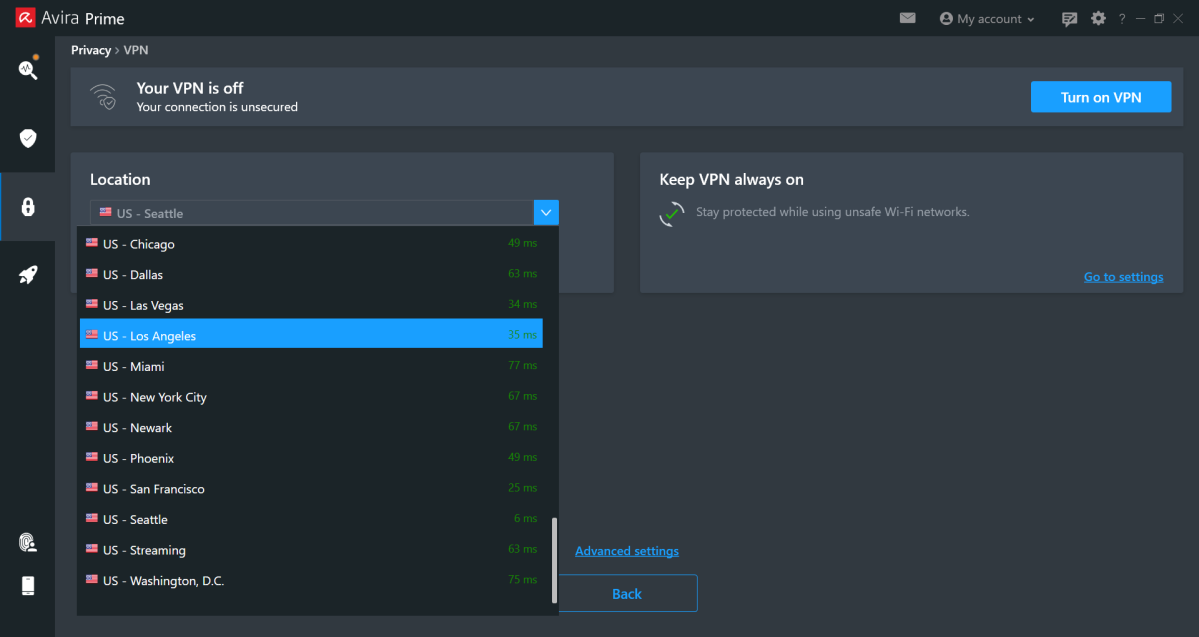
VPN
At first glance, a virtual private network may seem more in the realm of privacy protection — or circumventing geolocation restrictions. But privacy now often overlaps with security, especially if you find yourself on a public network. And that’s the primary utility of VPN services provided through an antivirus software plan.
A VPN acts as secure tunnel for data passing between your PC and the websites you visit. Because it’s encrypted, nobody snooping on the same network will be able to tell what servers you’re actually in contact with. They can only see that your PC is communicating with the VPN. So on a public network, anyone scoping out potential targets ends up with less info about your activity.
PCWorld
PCWorld
PCWorld
Of course, you must trust a VPN if you use one, because it ends up seeing all of your traffic. Typically, a reliable antivirus maker should meet this requirement — at least from a security perspective. Currently, AES 256-bit encryption is the standard. Don’t settle for less.
Also investigate the privacy policies — like how logs are kept (if they are). Be aware too that VPNs provided with antivirus plans don’t provide as much anonymity as independent services. You typically can’t pay anonymously, for example. (For more details, our VPN guide has the full rundown.)
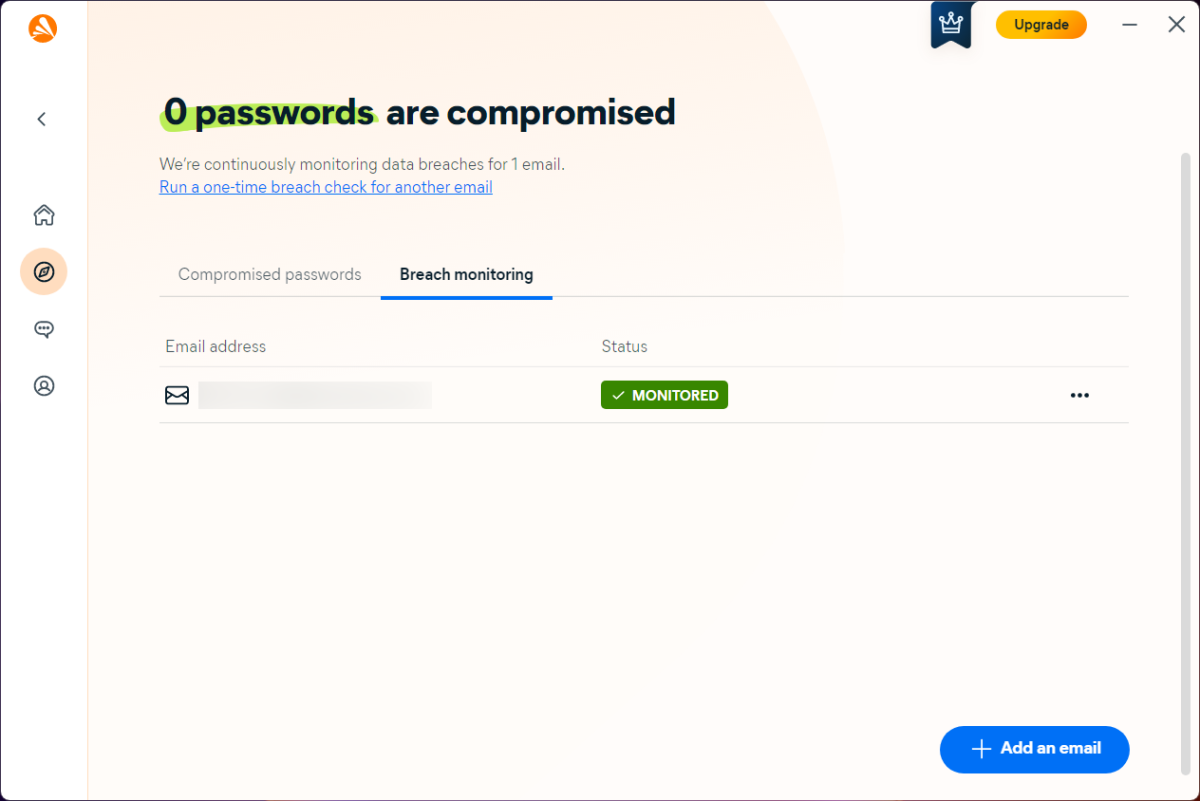
Dark web monitoring
An unfortunate reality is that websites get hacked, and that number continues to increase. Some weeks you’ll see near-daily news about ransomware, data breaches, and related occurrences.
The more sites you’ve used, the more likely your username and password have been stolen, and so too your real name, physical address, email address, phone number, birth date, social security number (if you live in the U.S.), and other such details. This info about you usually ends up on the dark web — a part of the internet where people share and sell illicit information, whether that’s stolen data or hacking tools.
PCWorld
PCWorld
PCWorld
Free tools exist to get alerts about data breaches and leaks (like Troy Hunt’s Have I Been Pwned site), but they don’t always catch everything. For dark web monitoring, your best offense is a wide defense. Antivirus software can be another set of metaphorical eyes helping keep watch. Most basic paid subscriptions will at least keep tabs on the email address associated with your account. Stepped up plans monitor more than one email address, along with credit card info, bank info, and personal details. (How much you share is up to you, based on your comfort with the antivirus company’s ability to keep those details safe.)
Good dark web monitoring will alert you quickly once new info surfaces — which helps you immediately change your password, enact a credit freeze, or take other protective measures based on what details leaked.
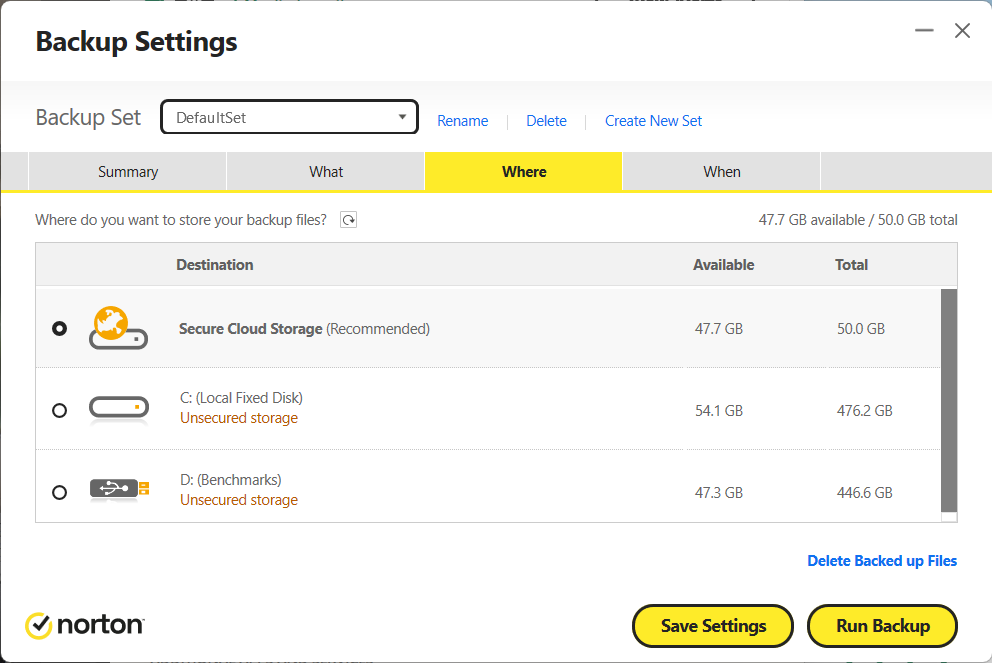
Cloud backups
With the prevalence of ransomware, a good backup system is a paramount part of defending your PC. Having a current backup of your files means no one can truly hold your PC hostage. They can encrypt your files and keep you from accessing them — but the backup lets you restore the lost files.
Usually, you’re on your own to do this, and properly at that, which involves the 3-2-1 method (three copies of the data, at least two different media types, and one kept off-site). Having cloud backup built into your antivirus software can help supplement and boost your current process. It serves as a different type of backup (compared to storing data on an external drive), and it also covers being off-site.
PCWorld
PCWorld
PCWorld
If an antivirus service offers this feature, make sure you’re getting cloud backup, rather than cloud storage. Cloud backup copies your files to the cloud, regardless of later changes made on your PC or other source device, and saves versions over time. Meanwhile, cloud storage mirrors files across all locations — if you delete a file on your hard drive, it disappears in the cloud, too. So this kind of setup will undermine the point of having a backup on hand.
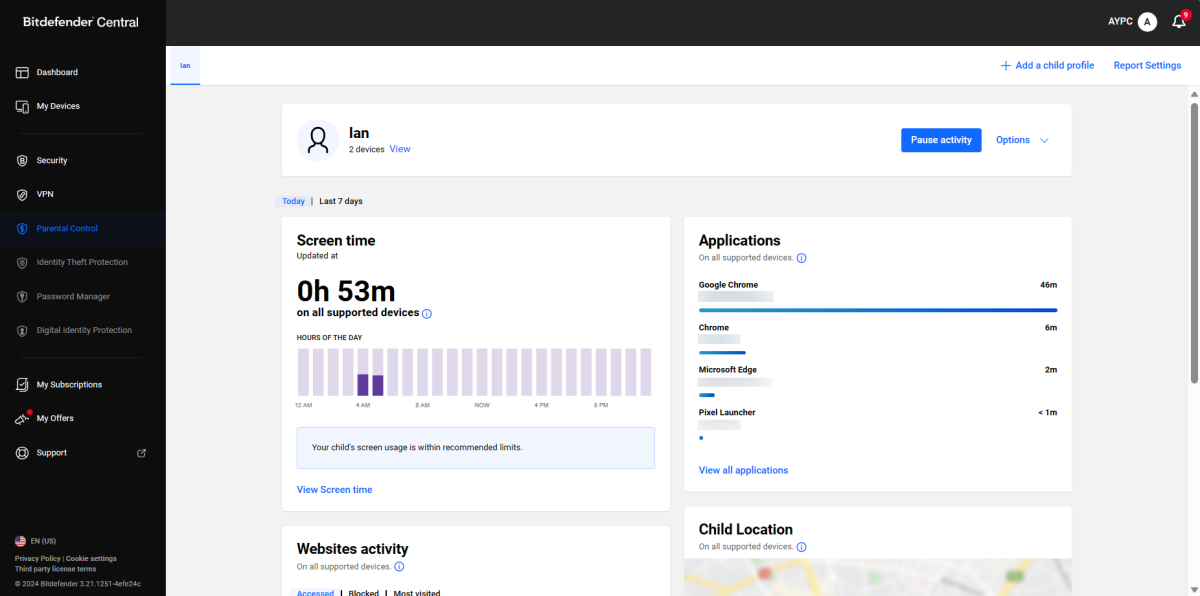
Parental controls
Not everything on the internet is appropriate for the tiny humans in our lives — and there’s not enough hours in the day to police all their online activity. Similarly, some adult family members don’t always pay attention to what types of sites are risky, which can cause headaches for both them and you.
Parental controls can help with managing these situations. Such tools allow you to filter and restrict online activity, with the better parental controls able to block specific sites and site categories on PCs and mobile devices (either universally or at specific times of day). They also can shut off internet access during certain hours, like during school or bedtime.
PCWorld
PCWorld
PCWorld
Separately, parental controls can also track location on mobile devices. However, compared to Android and iPhone’s built-in location tracking, this particular feature isn’t always as reliable. So when evaluating the usefulness of parental controls, focus more on their ability to restrict content and usage.
Data broker opt-out
Data brokers are the bottom-dwelling vacuum cleaners of the internet. They hoover up information about you from every corner — companies that sell your data (including places you shop), public records, social media, warranty registration info, and more. Those details then feed into people search sites, where entering a person’s name and city or state can reveal their current and past addresses, phone numbers, birth date, known relatives, judicial records, and even social security number.
Hackers can then use your personal data to wage social engineering attacks on you. Impersonating you when chatting with a customer service agent becomes much easier if they know your mother’s maiden name, the last few places you lived, your siblings’ names, and the like. That can then lead to identity theft and financial losses. And then at the far extreme end of dangerous behavior, someone can also use people finder sites for swatting attempts.
In response, entry and mid-tier level antivirus suites sometimes will scan for your info on data broker sites, using your email address, name, birthdate, or other identifying info, and see where you turn up. More expensive subscriptions will also automatically attempt to remove you from those sites, so that you don’t have to spend time filing requests for opt-out. Compared to dedicated opt-out services, this feature in an antivirus plan often isn’t as comprehensive, but the cost tends to be cheaper overall, too.
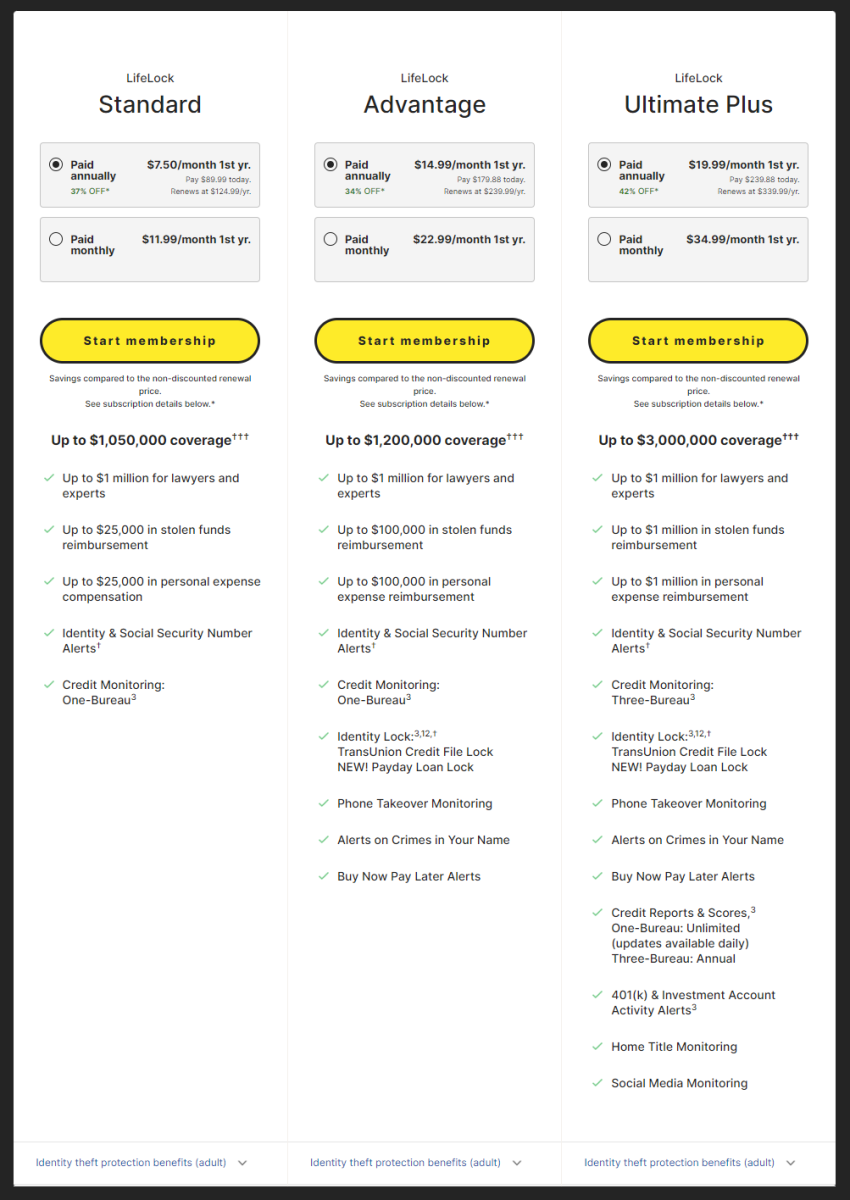
Identity protection
Identity theft is an ever-looming threat these days, thanks to untold data breaches. And while you may think antivirus software wouldn’t overlap, the more expensive subscriptions offer protections that start with identity monitoring. You’ll get a heads-up about things like changes to your credit, activity involving your social security number, phone number transfers (i.e., someone switches your cell phone provider, a possible sign of SIM jacking), even title changes if you own your home.
PCWorld
PCWorld
PCWorld
Top-tier plans may additionally include insurance-like coverage. If you’re ever victim of identity theft, you could get up to $1 million for remediation costs (having help reporting identity theft, restoring lost funds, etc).
Generally, you can handle identity threats and theft on your own, but this kind of service is meant as a time (and sanity) saver. The one potential drawback is the level of trust you’ll need to place in a third-party and their security practices, since they’ll end up learning much of your most sensitive information.
Social media privacy scan
If your social media accounts are set so that everything’s public, you can reveal a lot of personal information to strangers — people in your life, places you frequent, products you use or like. These details can then be used for social engineering hacks, or at a more extreme end of the scale, online or real-world stalking.
You can lock down your accounts on your own, but privacy settings can be annoying to find and change. So some antivirus software subscriptions (typically the more expensive plans) will offer to scan your social media settings to alert you to privacy issues. Think of this feature as not necessary, but potentially helpful if you’re too time-strapped to completely do it yourself.
PC utilities
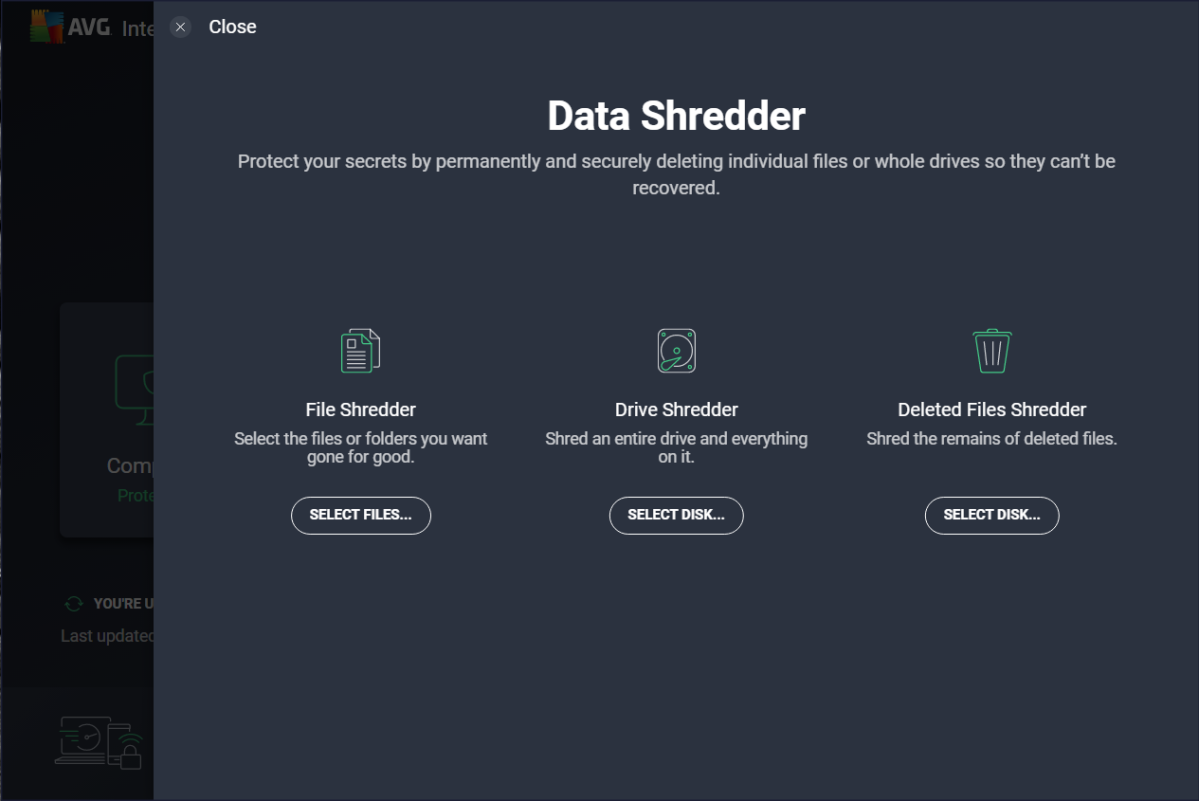
Data shredder
This kind of utility is a secure-delete tool for files — so long as they’re stored on a hard-disk drive. For solid-state drives (which most modern laptops and PCs use for storage), a different method is required for secure deletion.
Data shredders work by overwriting files repeatedly so the original data can’t be recovered. The better tools let you select the protocol used for the overwrite process, as well as how many passes are done.
PCWorld
PCWorld
PCWorld
System optimizer
You can already clean up Windows within the operating system itself — it has its own tools for deleting temporary files, dumping operating system installation files, and otherwise tidying up. But they’re not easily accessed through one simple interface, which is a gap some antivirus makers try to fill.
On the surface, a system optimizer utility can be helpful, but beware: You should first understand what you’re wiping beforehand. Altering your Windows registry in the name of spring cleaning could cause system issues down the road.
Mostly, if you know what you’re doing, system optimization tools can save a bit of time. But generally, most people shouldn’t buy an antivirus suite because it includes this kind of utility.
Software and driver updater
Software updates are definitely a key part of online security — out-of-date code leaves vulnerabilities open for bad actors to exploit. Some antivirus software monitors your apps and Windows for updates you’ve yet to run.
However, even though you can run updates directly through your antivirus software with this feature, you’re better off treating it as an alert system. Unless you’ll never update without outside assistance, most programs take care of their patches automatically, as does Windows. For the rare driver update that must be run manually, downloading the driver from the manufacturer website guarantees you run the right version. You’re usually best off getting updates direct from the source, to avoid potential version conflicts.
Sensitive file protection
You may have files you don’t want prying eyes to see — and while you could encrypt them, restricting access to them is sometimes an acceptable intermediary step.
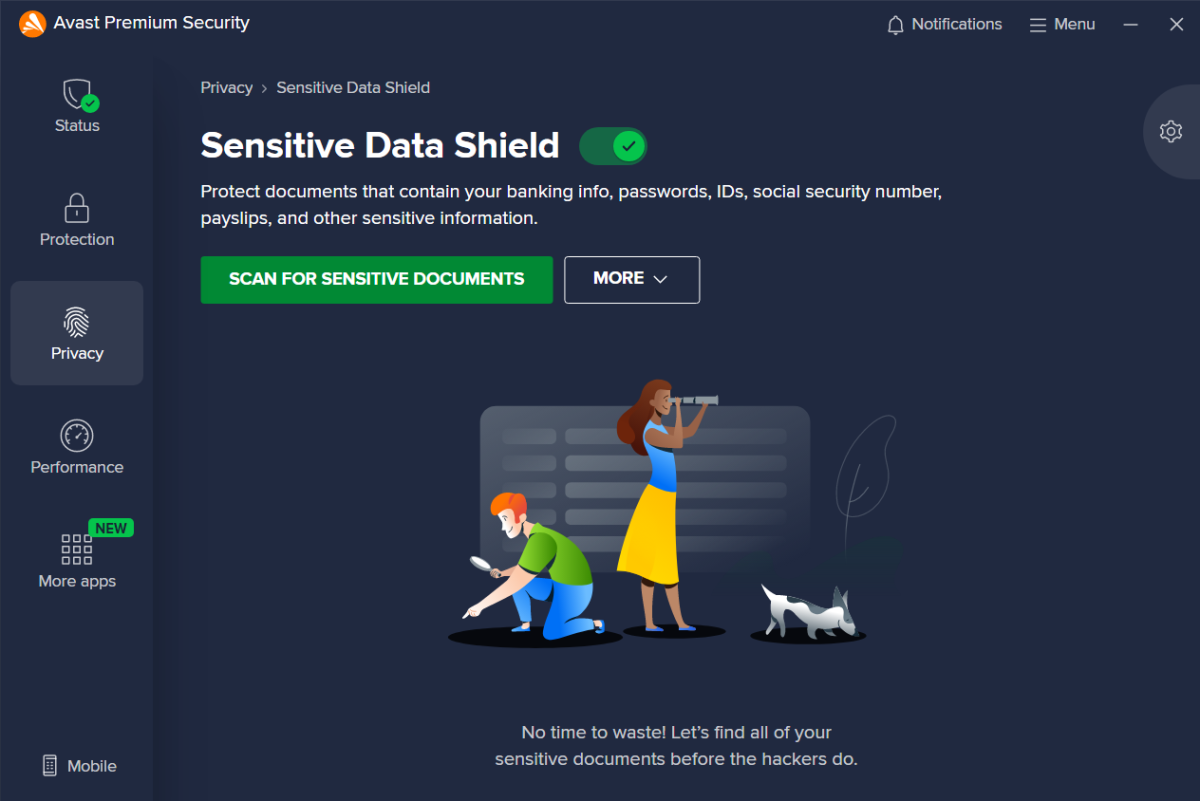
Sensitive Data Shield lets you find documents with highly personal information and restrict access to those files.
Sensitive Data Shield lets you find documents with highly personal information and restrict access to those files.
PCWorld
Sensitive Data Shield lets you find documents with highly personal information and restrict access to those files.
PCWorld
PCWorld
A few antivirus vendors include this feature with their software, which blocks general access to files and folders you’ve chosen. Instead, only specific apps can access them. So if you have a documents folder you specifically want to keep on lockdown, you can keep unapproved apps opening files in there. The idea is to prevent malicious or compromised apps from digging into documents you don’t want them in, unbeknownst to you.
In practice, this feature can be hit or miss—but when it does work reliably, you get a second line of light defense against snoops.
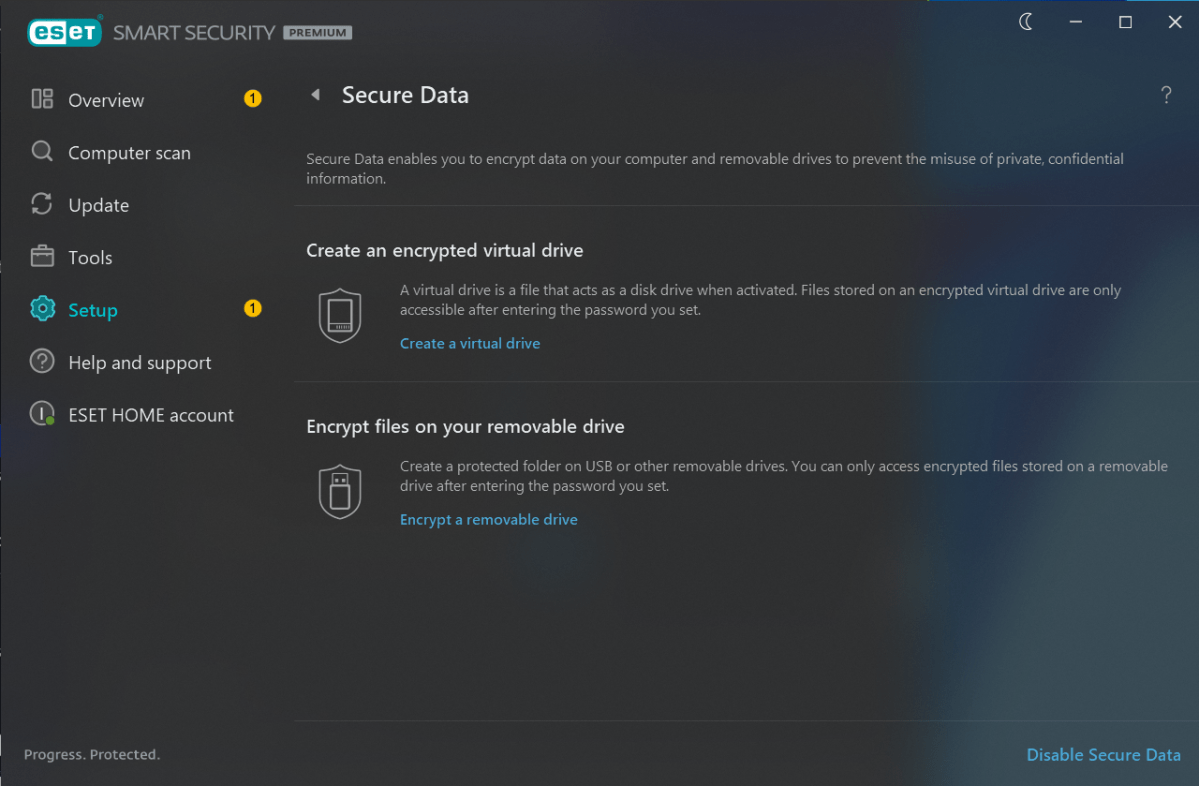
File encryption
This tool is a rarity, but it can dramatically boost the security of your sensitive files — even if you already encrypt your local storage drive.
Typically, antivirus software with this feature will let you create an encrypted container file, which then gets mounted on your PC as a virtual drive. Anything you store on that virtual drive will be locked down with said encryption once you unmount the container file.
Even if you already encrypt your whole storage drive using Windows Bitlocker, locking down individual files and folders this way adds extra protection. Why? If you’re logged into Windows, and someone gets access to your PC, Bitlocker won’t keep them from seeing your files. However, if the encrypted container file isn’t mounted, they won’t be able to see inside it.
PCWorld
PCWorld
PCWorld
When considering the usefulness of a file encryption feature, check if it uses at least 256-bit AES encryption — currently considered a standard level of protection. Pass on those that don’t.
Backup services
On rare occasion, you’ll see this utility in an antivirus suite, where you can use the software to run automated backups.
However, for this kind of feature (which is mission critical for your data and your overall sanity), we prefer dedicated software, which tends to be more robust. As appealing as an all-in-one software solution is, when it comes to backups, it’s best to choose an app based on how well it does the job.
Other things to consider
Customer service
If you need (or want) human assistance with your antivirus software, including basic walkthroughs of installing the app, some top-tier plans offer premium customer service.
Separately, top-tier plans also sometimes have agents available to help with identity theft — not just walking you through the process of remediation, but handling the details as well.
Scam protection tools
Phishing scams continue to get more sophisticated (and prevalent) over time — and in response, antivirus vendors have begun releasing tools to navigate around them. For example, McAfee now has a mobile app designed to automatically detect and block text messages containing phishing links.
Not all of these utilities are paid, either — Bitdefender’s Scamio chatbot is free. You just copy and paste a text link (or a screenshot of a text link), and it will tell you if it’s possibly dangerous. Similarly, you can paste in email or text messages to judge if the sender is genuine or just trying to play you.
See PCWorld’s guide to the best antivirus software for our recommendations.
Antivirus
But as protecting your PC became more complicated, vendors slowly morphed their offerings into full suites. Nowadays, a firewall and other safeguards like a browser extension, password manager, and VPN get dropped onto your system. You might even get a handful of utilities focused on optimizing your computer, rather than defending it.
To help you figure out what components are most important — as well as necessary for your situation — we’ve broken down the most common elements of today’s antivirus software.
Antivirus
At the heart of every antivirus plan is the engine that detects threats to your PC. These days, modern antivirus software both anticipates and roots out the presence of viruses and other malware, including ransomware.
Blocking malware before it even hits your computer is a key defense against situations like your PC being commandeered for botnet attacks, having your data stolen, and getting locked out of your documents and folders. It also can stop creepy behavior like being spied on through your webcam or having everything you do recorded (including what you type).
An antivirus engine does this by screening the websites you visit, as well as the email and apps on your PC, for phishing links and potential malicious downloads. Phishing attempts usually try to steal your passwords, credit card details, or other personal information by pretending to be a legitimate site and then capturing whatever data you input.

Ed Hardie
Ed Hardie
Ed Hardie
The other half of the protection comes from the antivirus engine’s ability to detect and then eliminate malware that does land on your PC. Typically, this monitoring happens in at least two forms: Real-time scanning watches for changed or new files, as well as unusual behavior from apps and Windows itself. Scheduled scans (especially if they’re full system scans) dig into your PC to make sure nothing was missed by the real-time scanning.
Antivirus apps and virus definitions get continual updates as new malware appears in the wild. So long as you buy a subscription from a reputable company (like those reviewed by leading security organizations AV-Test and AV-Comparatives), you’ll be kept up to date for your whole term. That applies even if you bought a plan labeled as 2024 and the year crosses over into 2025.
The plan you buy will dictate how many devices are covered — usually subscriptions support macOS, Android, and iOS gear in addition to Windows PCs. On rare occasion, Chromebooks are supported as well.
Firewall
Traffic doesn’t just go to your computer, but from it, too — and depending on the app, that data may contain info you don’t want to fall into the wrong hands. A malicious app can spy on what you’re doing, and then transmit that to a would-be hacker. A good firewall blocks those attempts automatically.
A reliable firewall also closes networking ports on your PC, so that unknown parties can’t connect and find a way into your home network. Think of it like a house where shutting the external doors causes them to blend into the walls, making it difficult to discern. However, if a door is left open, someone could walk in and then take what they want, set up cameras to spy on you, or change your phone settings to forward all text messages to them, among other things. A firewall is a bit like a guard that always stays alert, making sure no one can get in.
Browser extensions
The most common add-on to your browser (be it Edge, Chrome, or Firefox) is one designed for online protection. Usually, it’ll at least add extra icons to search results to warn you away from suspicious sites. The better ones also block trackers and ads to defend your privacy and help you avoid malvertising — that is, malware spread through compromised ad networks.

PCWorld
PCWorld
PCWorld
Other extensions help tie your browser into components of the overall antivirus suite, making their use seamless. Most often you’ll see one for a password manager get installed, so that you can capture, create, and use entries in your vault.
On occasion, you’ll see antivirus suites that offer plugins for shopping coupons and deals. These are not related to security at all, and can actually conflict with keeping your privacy.
Password manager
These days online security extends beyond simply defending your PC against malware. That’s why today’s software also blocks phishing websites, which generally try to capture sensitive information (like your login info) by pretending to be a legitimate site. If your credentials get stolen, you could end up with problems ranging from unwanted credit card purchases all the way to full-blown identity theft.
By using a password manager, you can prevent the simplest form of account hacking — credential stuffing. A bad actor takes usernames and passwords leaked through data breaches, then tries them across the web to see what else can be accessed with that same login info. Since some people reuse their passwords, attackers can breach a whole new set of accounts easily.

PCWorld
PCWorld
PCWorld
Password managers let you generate strong, unique credentials, which thwarts this kind of hack. They also take away the burden of trying to remember dozens (if not hundreds) of secure passwords. And with data leaks and breaches so commonplace nowadays, these services make changing your password far simpler and faster, too.
VPN
At first glance, a virtual private network may seem more in the realm of privacy protection — or circumventing geolocation restrictions. But privacy now often overlaps with security, especially if you find yourself on a public network. And that’s the primary utility of VPN services provided through an antivirus software plan.
A VPN acts as secure tunnel for data passing between your PC and the websites you visit. Because it’s encrypted, nobody snooping on the same network will be able to tell what servers you’re actually in contact with. They can only see that your PC is communicating with the VPN. So on a public network, anyone scoping out potential targets ends up with less info about your activity.

PCWorld
PCWorld
PCWorld
Of course, you must trust a VPN if you use one, because it ends up seeing all of your traffic. Typically, a reliable antivirus maker should meet this requirement — at least from a security perspective. Currently, AES 256-bit encryption is the standard. Don’t settle for less.
Also investigate the privacy policies — like how logs are kept (if they are). Be aware too that VPNs provided with antivirus plans don’t provide as much anonymity as independent services. You typically can’t pay anonymously, for example. (For more details, our VPN guide has the full rundown.)
Dark web monitoring
An unfortunate reality is that websites get hacked, and that number continues to increase. Some weeks you’ll see near-daily news about ransomware, data breaches, and related occurrences.
The more sites you’ve used, the more likely your username and password have been stolen, and so too your real name, physical address, email address, phone number, birth date, social security number (if you live in the U.S.), and other such details. This info about you usually ends up on the dark web — a part of the internet where people share and sell illicit information, whether that’s stolen data or hacking tools.

PCWorld
PCWorld
PCWorld
Free tools exist to get alerts about data breaches and leaks (like Troy Hunt’s Have I Been Pwned site), but they don’t always catch everything. For dark web monitoring, your best offense is a wide defense. Antivirus software can be another set of metaphorical eyes helping keep watch. Most basic paid subscriptions will at least keep tabs on the email address associated with your account. Stepped up plans monitor more than one email address, along with credit card info, bank info, and personal details. (How much you share is up to you, based on your comfort with the antivirus company’s ability to keep those details safe.)
Good dark web monitoring will alert you quickly once new info surfaces — which helps you immediately change your password, enact a credit freeze, or take other protective measures based on what details leaked.
Cloud backups
With the prevalence of ransomware, a good backup system is a paramount part of defending your PC. Having a current backup of your files means no one can truly hold your PC hostage. They can encrypt your files and keep you from accessing them — but the backup lets you restore the lost files.
Usually, you’re on your own to do this, and properly at that, which involves the 3-2-1 method (three copies of the data, at least two different media types, and one kept off-site). Having cloud backup built into your antivirus software can help supplement and boost your current process. It serves as a different type of backup (compared to storing data on an external drive), and it also covers being off-site.

PCWorld
PCWorld
PCWorld
If an antivirus service offers this feature, make sure you’re getting cloud backup, rather than cloud storage. Cloud backup copies your files to the cloud, regardless of later changes made on your PC or other source device, and saves versions over time. Meanwhile, cloud storage mirrors files across all locations — if you delete a file on your hard drive, it disappears in the cloud, too. So this kind of setup will undermine the point of having a backup on hand.
Parental controls
Not everything on the internet is appropriate for the tiny humans in our lives — and there’s not enough hours in the day to police all their online activity. Similarly, some adult family members don’t always pay attention to what types of sites are risky, which can cause headaches for both them and you.
Parental controls can help with managing these situations. Such tools allow you to filter and restrict online activity, with the better parental controls able to block specific sites and site categories on PCs and mobile devices (either universally or at specific times of day). They also can shut off internet access during certain hours, like during school or bedtime.

PCWorld
PCWorld
PCWorld
Separately, parental controls can also track location on mobile devices. However, compared to Android and iPhone’s built-in location tracking, this particular feature isn’t always as reliable. So when evaluating the usefulness of parental controls, focus more on their ability to restrict content and usage.
Data broker opt-out
Data brokers are the bottom-dwelling vacuum cleaners of the internet. They hoover up information about you from every corner — companies that sell your data (including places you shop), public records, social media, warranty registration info, and more. Those details then feed into people search sites, where entering a person’s name and city or state can reveal their current and past addresses, phone numbers, birth date, known relatives, judicial records, and even social security number.
Hackers can then use your personal data to wage social engineering attacks on you. Impersonating you when chatting with a customer service agent becomes much easier if they know your mother’s maiden name, the last few places you lived, your siblings’ names, and the like. That can then lead to identity theft and financial losses. And then at the far extreme end of dangerous behavior, someone can also use people finder sites for swatting attempts.
In response, entry and mid-tier level antivirus suites sometimes will scan for your info on data broker sites, using your email address, name, birthdate, or other identifying info, and see where you turn up. More expensive subscriptions will also automatically attempt to remove you from those sites, so that you don’t have to spend time filing requests for opt-out. Compared to dedicated opt-out services, this feature in an antivirus plan often isn’t as comprehensive, but the cost tends to be cheaper overall, too.
Identity protection
Identity theft is an ever-looming threat these days, thanks to untold data breaches. And while you may think antivirus software wouldn’t overlap, the more expensive subscriptions offer protections that start with identity monitoring. You’ll get a heads-up about things like changes to your credit, activity involving your social security number, phone number transfers (i.e., someone switches your cell phone provider, a possible sign of SIM jacking), even title changes if you own your home.

PCWorld
PCWorld
PCWorld
Top-tier plans may additionally include insurance-like coverage. If you’re ever victim of identity theft, you could get up to $1 million for remediation costs (having help reporting identity theft, restoring lost funds, etc).
Generally, you can handle identity threats and theft on your own, but this kind of service is meant as a time (and sanity) saver. The one potential drawback is the level of trust you’ll need to place in a third-party and their security practices, since they’ll end up learning much of your most sensitive information.
Social media privacy scan
If your social media accounts are set so that everything’s public, you can reveal a lot of personal information to strangers — people in your life, places you frequent, products you use or like. These details can then be used for social engineering hacks, or at a more extreme end of the scale, online or real-world stalking.
You can lock down your accounts on your own, but privacy settings can be annoying to find and change. So some antivirus software subscriptions (typically the more expensive plans) will offer to scan your social media settings to alert you to privacy issues. Think of this feature as not necessary, but potentially helpful if you’re too time-strapped to completely do it yourself.
PC utilities
Data shredder
This kind of utility is a secure-delete tool for files — so long as they’re stored on a hard-disk drive. For solid-state drives (which most modern laptops and PCs use for storage), a different method is required for secure deletion.
Data shredders work by overwriting files repeatedly so the original data can’t be recovered. The better tools let you select the protocol used for the overwrite process, as well as how many passes are done.

PCWorld
PCWorld
PCWorld
System optimizer
You can already clean up Windows within the operating system itself — it has its own tools for deleting temporary files, dumping operating system installation files, and otherwise tidying up. But they’re not easily accessed through one simple interface, which is a gap some antivirus makers try to fill.
On the surface, a system optimizer utility can be helpful, but beware: You should first understand what you’re wiping beforehand. Altering your Windows registry in the name of spring cleaning could cause system issues down the road.
Mostly, if you know what you’re doing, system optimization tools can save a bit of time. But generally, most people shouldn’t buy an antivirus suite because it includes this kind of utility.
Software and driver updater
Software updates are definitely a key part of online security — out-of-date code leaves vulnerabilities open for bad actors to exploit. Some antivirus software monitors your apps and Windows for updates you’ve yet to run.
However, even though you can run updates directly through your antivirus software with this feature, you’re better off treating it as an alert system. Unless you’ll never update without outside assistance, most programs take care of their patches automatically, as does Windows. For the rare driver update that must be run manually, downloading the driver from the manufacturer website guarantees you run the right version. You’re usually best off getting updates direct from the source, to avoid potential version conflicts.
Sensitive file protection
You may have files you don’t want prying eyes to see — and while you could encrypt them, restricting access to them is sometimes an acceptable intermediary step.

Sensitive Data Shield lets you find documents with highly personal information and restrict access to those files.
Sensitive Data Shield lets you find documents with highly personal information and restrict access to those files.
PCWorld
Sensitive Data Shield lets you find documents with highly personal information and restrict access to those files.
PCWorld
PCWorld
A few antivirus vendors include this feature with their software, which blocks general access to files and folders you’ve chosen. Instead, only specific apps can access them. So if you have a documents folder you specifically want to keep on lockdown, you can keep unapproved apps opening files in there. The idea is to prevent malicious or compromised apps from digging into documents you don’t want them in, unbeknownst to you.
In practice, this feature can be hit or miss—but when it does work reliably, you get a second line of light defense against snoops.
File encryption
This tool is a rarity, but it can dramatically boost the security of your sensitive files — even if you already encrypt your local storage drive.
Typically, antivirus software with this feature will let you create an encrypted container file, which then gets mounted on your PC as a virtual drive. Anything you store on that virtual drive will be locked down with said encryption once you unmount the container file.
Even if you already encrypt your whole storage drive using Windows Bitlocker, locking down individual files and folders this way adds extra protection. Why? If you’re logged into Windows, and someone gets access to your PC, Bitlocker won’t keep them from seeing your files. However, if the encrypted container file isn’t mounted, they won’t be able to see inside it.

PCWorld
PCWorld
PCWorld
When considering the usefulness of a file encryption feature, check if it uses at least 256-bit AES encryption — currently considered a standard level of protection. Pass on those that don’t.
Backup services
On rare occasion, you’ll see this utility in an antivirus suite, where you can use the software to run automated backups.
However, for this kind of feature (which is mission critical for your data and your overall sanity), we prefer dedicated software, which tends to be more robust. As appealing as an all-in-one software solution is, when it comes to backups, it’s best to choose an app based on how well it does the job.
Other things to consider
Customer service
If you need (or want) human assistance with your antivirus software, including basic walkthroughs of installing the app, some top-tier plans offer premium customer service.
Separately, top-tier plans also sometimes have agents available to help with identity theft — not just walking you through the process of remediation, but handling the details as well.
Scam protection tools
Phishing scams continue to get more sophisticated (and prevalent) over time — and in response, antivirus vendors have begun releasing tools to navigate around them. For example, McAfee now has a mobile app designed to automatically detect and block text messages containing phishing links.
Not all of these utilities are paid, either — Bitdefender’s Scamio chatbot is free. You just copy and paste a text link (or a screenshot of a text link), and it will tell you if it’s possibly dangerous. Similarly, you can paste in email or text messages to judge if the sender is genuine or just trying to play you.
See PCWorld’s guide to the best antivirus software for our recommendations.
Antivirus