Enlarge / The Nothing Phone 2 all lit up. (credit: Ron Amadeo)
It turns out companies that stonewall the media's security questions actually aren't good at security. Last Tuesday, Nothing Chats—a chat app from Android manufacturer "Nothing" and upstart app company Sunbird—brazenly claimed to be able to hack into Apple's iMessage protocol and give Android users blue bubbles. We immediately flagged Sunbird as a company that had been making empty promises for almost a year and seemed negligent about security. The app launched Friday anyway and was immediately ripped to shreds by the Internet for many security issues. It didn't last 24 hours before Nothing pulled the app from the Play Store Saturday morning. The Sunbird app, which Nothing Chat is just a reskin of, has also been put "on pause."
The initial sales pitch for this app—that it would log you into iMessage on Android if you handed over your Apple username and password—was a huge security red flag that meant Sunbird would need an ultra-secure infrastructure to avoid disaster. Instead, the app turned out to be about as unsecure as you could possibly be. Here's Nothing's statement:
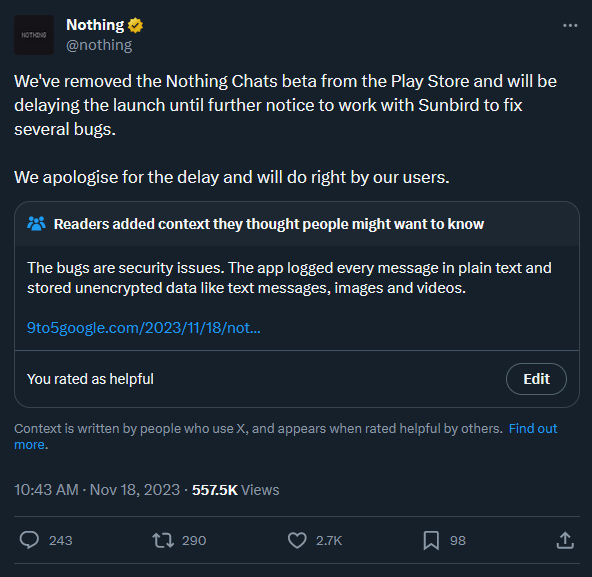
Nothing Chat's shut down post. (credit: Twitter)
How bad are the security issues? Both 9to5Google and Text.com (which is owned by Automattic, the company behind WordPress) uncovered shockingly bad security practices. Not only was the app not end-to-end encrypted, as claimed numerous times by Nothing and Sunbird, but Sunbird actually logged and stored messages in plain text on both the error reporting software Sentry and in a Firebase store. Authentication tokens were sent over unencrypted HTTP so this token could be intercepted and used to read your messages.
Read 7 remaining paragraphs | Comments